Safeguard Against Security Breaches, Data Loss, Downtime and Disruption.
Our range of security offerings provides peace of mind for businesses with best-practice global vendors specialising in network security, cyber security, awareness, and assessments.
Don’t wait for a breach to happen—be proactive in fortifying your defences. Let saberVox be your reliable partner in strengthening your cybersecurity posture.
We work with businesses towards comprehensive IT network and device security monitoring and can help businesses meet their cyber insurance requirements.
By partnering with us, you can take your cybersecurity to the next level and continuously evolve your practices to stay ahead of evolving threats. Our team of seasoned security experts will be your trusted guides, leading you on the safest and most secure path forward.

cyberWise Security Awareness Training
These fundamental steps can help towards becoming cybersecurity compliant and help towards the Essential Eight maturity model and cyber insurance coverage.
Sabervox also recommends our staff security awareness training product, cyberWise, as a first line of defence against security threats to your business.
Essential Eight
One of the first steps towards being more cyber secure is by referencing the Essential Eight framework.
The Australian Cyber Security Centre has developed mitigation strategies to help organisations protect themselves against various cyber threats. The most effective of these mitigation strategies are the Essential Eight.
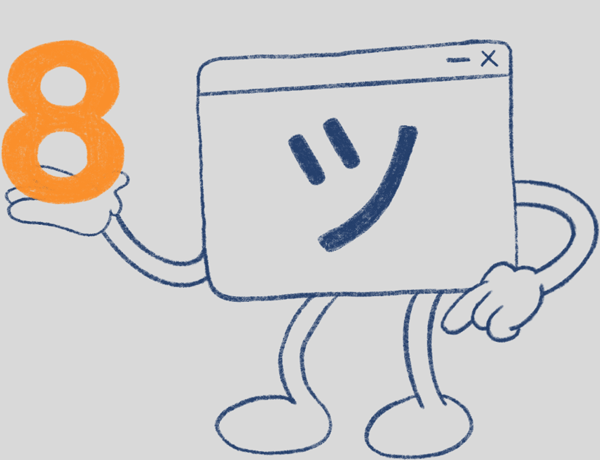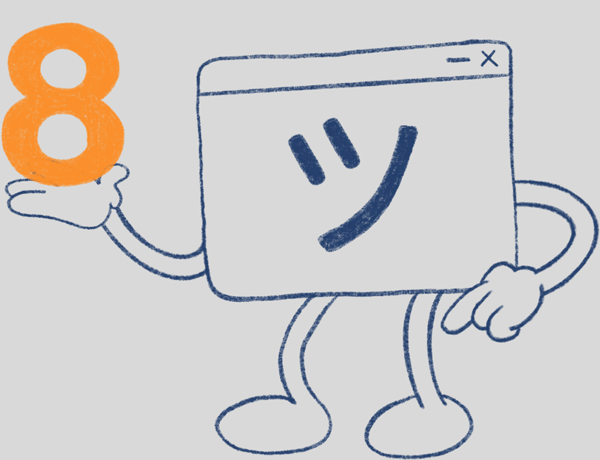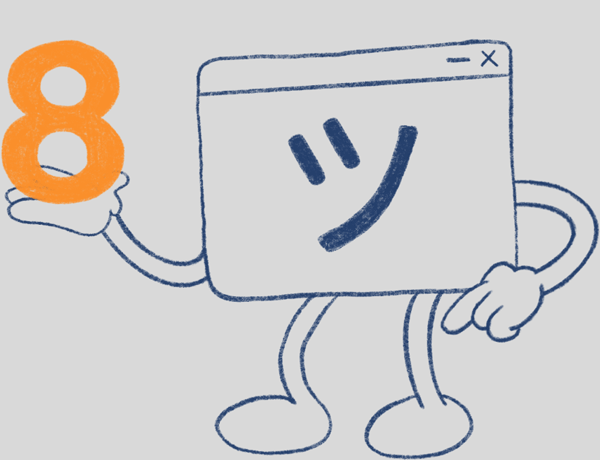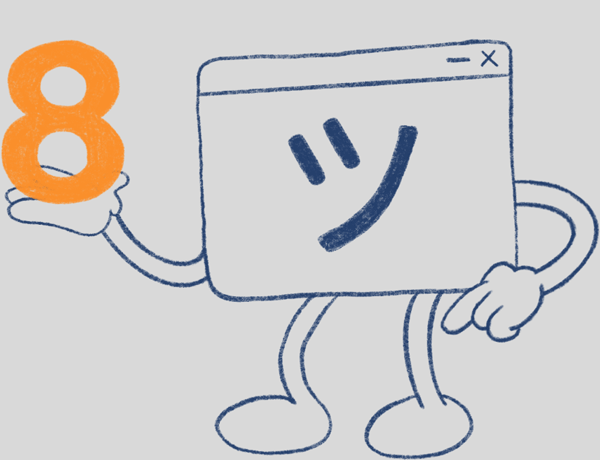
The mitigation strategies that constitute the Essential Eight are:
Application control
Patch applications

Configure Microsoft Office macro settings

User application hardening

Restrict administrative privileges

Patch operating systems

Multi-factor authentication